When developing iOS applications that require user authentication, It’s not unusual for teams to have some sort of express login for Qa authentication. Express login lets testers and developers access the app quickly for testing purposes, simulating real-world scenarios without having to input Qa passwords repeatedly. As we all know Securely managing sensitive information like passwords is of utmost importance. In a QA (Quality Assurance) environment, having to input these Qa passwords repeatedly when testing can be annoying while also risking potential security breaches. To overcome this, we can leverage Xcode scheme’s environment variables, which allows developers to store sensitive data, such as QA passwords, securely without having to hard-code them into our source code.
Understanding Xcode Scheme’s Environment Variables
Environment variables are dynamic values that can be accessed by our apps at runtime. In Xcode, we can use environment variables to store API keys and QA secrets like password, as well as other configuration parameters, such as URLs and feature flags that can be accessed at runtime. This allows us to store sensitive information, reducing the risk of accidental exposure.
Setting Up Environment Variables in Xcode
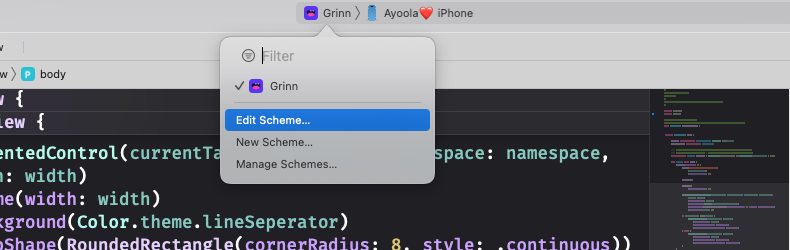
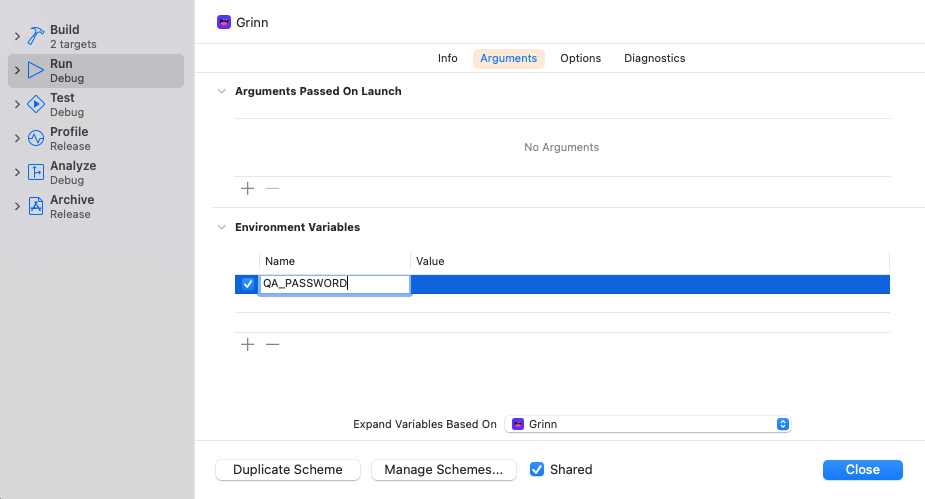
To begin using environment variables in our Xcode project, we must add them through Xcode’s scheme editor. Access the scheme editor by using the edit scheme option in the project window toolbar and then select the Run step on the left side of the scheme editor. Click the Arguments button at the top of the scheme editor to access the environment variables. Use the Add (+) button to add the environment variables. From there, we can easily include the desired environment variables for our app. Here are the visual steps:
Navigation to Xcode Scheme Editor
Adding key value pairs Environment Variables in Xcode Scheme Editor
Access the Environment Variables in Swift
With the environment variable approach in place, we can now use the ProcessInfo class to retrieve the value. This class contains a property named "processInfo," which holds a dictionary containing various values. The name of the environment variable serves as a key in this dictionary. By using this key, we can access the corresponding qa password in our environment variable’s value and use it to power express login in our QA environment without compromising the security of the app.
1
2
3
4
5
guard let qaPassword = ProcessInfo.processInfo.environment["QA_PASSWORD"] else {
fatalError("QA password not set in the environment variables.")
}
// Now we can use 'qaPassword' wherever we need the QA password in our app.
Caveat
It’s important to note that while environment variables are an excellent way to manage sensitive data during development and testing, they will not be available in a production environment on iOS devices. iOS apps are sandboxed, which means they operate in a restricted environment, isolated from the rest of the system for security reasons.
To handle sensitive data in production environment, it’s essential to use secure and industry-standard practices. Here are a few approaches commonly used in production: Keychain Services, a secure configuration file that is not included in the app’s source code but is provided during the build process. This configuration file can be read by the app at runtime, allowing you to provide the necessary API keys and secrets specific to the production environment. Additionally, you can use encryption or other security measures to protect the data within the configuration file.
Conclusion
By using Xcode environment variables to store QA passwords for express login, we can enhance the lives of our Qa testers while still maintaining a level of security during the testing process. This approach keeps sensitive data out of your source code and allows for a more controlled and secure testing environment. Remember to follow best practices to protect the environment variables and regularly update passwords to maintain the integrity of your app’s security. Happy coding!
